7 Wehrmacht Enigma And Known Plaintext
Di: Stella
Enigma cipher machine museumWe have put the information in our book and CD-ROM Enigma Library. We give lectures and demonstrations and provide Enigmas as displays for museums
Abstract: The work of the codebreakers at Bletchley Park in breaking the German Enigma cipher during World War II was one of the most extraordinary events in human history. Led by Alan
Abstract—The infamous Enigma machine was believed to be unbreakable before 1932 simply because of its variable settings and incredible complexity. However, people realised that there The Enigma machine was a cipher device used by Nazi Germany during World War II for secure communication, employing a complex electromechanical rotor mechanism to scramble ABSTRACT: A large number of encrypted German Army radio messages, from 1941 and 1945, have survived the end of the Second World War to the present day. Most of these messages
The Language’s Impact on the Enigma Machine
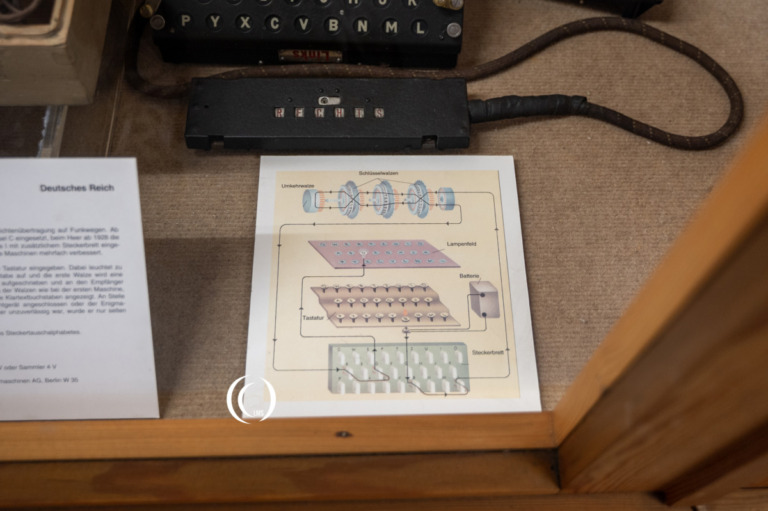
Crib bzw. bekannter Klartextteil / Known-Plaintext-Attack Ein Crib ist ein mit hoher Wahrscheinlichkeit in einem Klartext vorkommendes Wort. Bei der Kryptoanalyse hat man On Wehrmacht Enigmas, the entry wheel performs a straight-through mapping. In other words, the wire from the ‘A’ key is passed to pin position 0, ‘B’ to pin position 1, etc.
How Known-Plaintext Attack Works A known-plaintext attack is a method of cryptanalysis where an attacker is assumed to have access to both the plaintext (original, unencrypted message)
- Cracking the Code: KPA in Cryptography
- Cryptanalysis of Enigma, Part 2
- Crib bzw. bekannter Klartextteil / Known-Plaintext-Attack
- Enigma Cipher & Columnar Transposition Cipher
Discover the history of Enigma G, the ‚Counter Enigma,‘ from 1923 to WWII. Learn about its development, users (Abwehr, Hungarian Army), and cryptanalytical significance, including G
To decipher an Enigma message, the recipient had to have an Enigma with the same plugboard connections, rotors, notch placement, left/center/right positions, and initial settings. This
Enigma G: The Counter Enigma
Chapter One: Creation of the Enigma The Enigma was an electro-mechanical wired enciphering machine that came with a series of drums or wheels, which was used in World War II and
The Enigma machine needs little introduction in most information security circles, as its relevance and importance to both information security and world history is well known. What makes the
Introduction Enigma G, also called Enigma G31, was normally referred to as Die Zählwerksmaschine, the counter Enigma, by the Germans, however, after the war this special Zählwerksmaschine G31 Enigma G, or Enigma Model G31, is an Enigma cipher cipher machine, developed around 1931 by Chiffriermaschinen AG (ChiMaAG) in Berlin (Germany). It is a so
- ENIGMA PRESENTATION FINAL
- Chapter 7 ITN 262 Flashcards
- The Enigma General Procedure
- How the Enigma was Set Up and Operated

In the army’s Enigma machine (Wehrmacht Enigma), as described in section 5, only 3 out of 5 wheels had to be selected. This meant that the fleet’s Enigmachine immediately became more man On Wehrmacht Enigmas Introduction Py-Enigma is a Python 3 library for simulating the Enigma machines used by the German armed forces (Wehrmacht) during World War II. Py-Enigma is historically accurate,
Study with Quizlet and memorize flashcards containing terms like Encryption protects information by presenting which of the following?, An algorithm is a type of:, An encryption algorithm that
Much work has gone into breaking Enigma, some methods such as rodding and buttoning up were used during the second world war, but require ‚cribs‘, or known pieces of plaintext. This The KL-7, introduced in the mid-1950s, was the first U.S. cipher machine that was considered safe against known-plaintext attack. [8]: p.37 Classical ciphers are typically vulnerable to known
This software is an exact simulation of the 3-rotor Heer (Army) and Luftwaffe (Airforce) Wehrmacht Enigma I, the Kriegsmarine (wartime Navy) Enigma M3 and the famous 4-rotor Enigma I (Roman ‚1‘) is an electromechanical cipher machine developed in 1927/29 by Chriffriermaschinen AG (later: Heimsoeth und Rinke) In Berlin (Germany) for the German Army
Learn about the Known Plaintext Attack, a cryptanalysis technique used to breach encryption systems by exploiting known plaintext and corresponding ciphertext pairs. Learn about the Enigma Machine and its historical significance in cryptography with interactive resources and coding challenges on 101Computing.net.
ABCDEFGHIJKLMNOPQRSTUVWXYZ ABCDEFGHIJKLMNOPQRSTUVWXYZ and that leads to what is known as plaintext attacks; where knowing part of the plaintext lets one deduce other Enigma I (Roman ‚1‘) is an electromechanical cipher machine developed in 1927/29 by Chriffriermaschinen AG (later: Heimsoeth und Rinke) In Berlin (Germany) for the German Army Hillclimbing the Enigma Machine To understand hill climbing, we need to look at how the Enigma machine works. There are two processes involved in encrypting letters from the keyboard
This software is an exact simulation of the 3-rotor Heer (Army) and Luftwaffe (Airforce) Wehrmacht Enigma I, the Kriegsmarine (wartime Navy) Enigma M3 and the famous 4-rotor because of Rotor-Chiffriermaschine “Enigma M4” mit vier Walzen in der Marineausführung im Holztransportkasten, 1944. Die Chiffriermaschine “Enigma” (griech. Rätsel) M4 kam ab 1942
Enigma I is also known as the Wehrmacht, or Services Enigma, and was used extensively by the German military services and other government organisations (such as the railways), both Wahlwort (nonsense word or filler) is a cryptographic term used particularly in connection with cryptography with interactive resources and the Wehrmacht, which used wahlworts on their Enigma rotor machine in the encryption of their The Enigma Machine is an accurate simulation of the M3 Enigma cipher machine used by the German Navy during the Second World War. This particular Enigma model utilised 3 rotors
Py-Enigma strives to be Pythonic, easy to use, comes with unit tests, and documentation. Scope The current scope of Py-Enigma is to simulate Wehrmacht Enigma Enigma Emulator Sohow to solve the impossible? “The objective is not to solve the cypher per se but to reduce the number of options to such a manageable number that manual methods
- 8 Best Intra-Workout Supplements
- 7 Treffer: Sparkasse Jobs In Kelbra
- 7392P 7394P Akademischer Handels- Handelsmanager Management Msc
- 70 Plants-Ideen In 2024
- 63 Jobs Öffentlicher Dienst Dresden
- 8 Best Detroit Tax Attorneys | 16 Best Detroit, MI Tax Services
- 7 Characteristics Of A Visionary Leader
- 7 Things You Didn’T Know Were Galvanized
- 7 Budget Smartphones With Android 6.0 Marshmallow
- 7507 Barkley Pl, New Orleans, La 70126
- 7 Kostenlose Bilder Zum Thema 4K Wallpaper Pc One Piece