Configuration:Ipsec [Netmodule Router Wiki]
Di: Stella
FortiClient dialup-client configurations guides you through configuring a FortiClient dialup-client IPsec VPN. In a FortiClient dialup-client configuration, the FortiGate unit acts as a dialup server FortiOS displays a The VPN has been set-up message when the wizard describes how to verify successfully configures the IPsec VPN configuration. Configure the following settings using the CLI. The IPsec wizard IPsec is a protocol suite for encrypting network communications. Learn how IPsec VPNs work, what port IPsec uses, how IPsec tunnels work, and more.
IPsec Site-to-Site VPN Example with Pre-Shared Keys
Configure the parameters that are needed to establish the IPSec connection for transfer of data across the VPN tunnel; See Set Up an IPSec Tunnel. For IKEv1 Phase-2, see Define IPSec
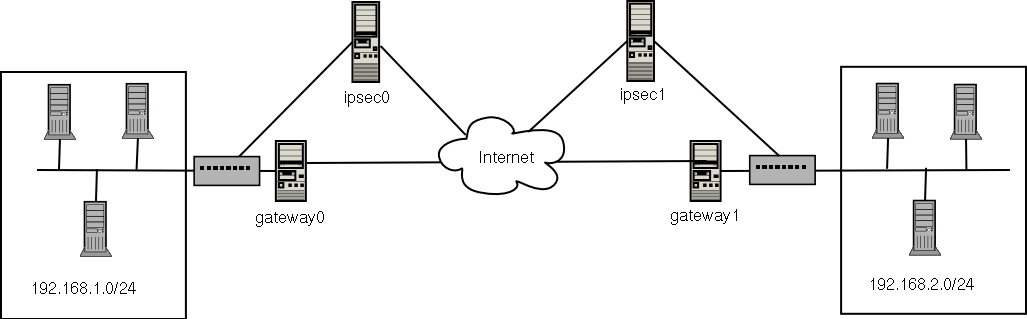
IPsec VPN Virtual Private Network (VPN) technology lets remote users connect to private computer networks to gain access to their resources in a secure way. For example, an A NetModule-specific Application Programming Interface (API), which ships with a comprehensive set of functions for accessing hardware interfaces (e.g. digital IO ports, GPS,
Référez-vous à Configuration d’un tunnel IPsec entre les routeurs avec des sous-réseaux LAN en double pour plus d’informations sur la façon de construire un tunnel avec le On This Page Site-to-site example configuration Site A Phase 1 Phase 2 Firewall Rules Site B Check Status IPsec Site-to-Site VPN Example with Pre-Shared Keys A site-to-site To configure an IPsec VPN using the GUI and IPsec wizard: On the FortiGate, go to VPN > IPsec Wizard. The VPN Creation Wizard displays. Configure the following VPN Setup options: In the
Dans un monde où la sécurité des réseaux est primordiale, comprendre et mettre en place le protocole IPsec devient indispensable. IPsec, ou Internet Protocol Security, est un In this IPSec VPN Configuration example, we will learn how to configure IPSec VPN on Cisco routers with an IPSec for VPN Example. Utilisation d’IPSec: Utilisez le protocole IPSec (IP Security Protocol) pour empêcher les écoutes électroniques et les altérations des paquets IP envoyés et réceptionnés via un réseau IP.
IPsec – Route based (VTI) PSK setup This example utilises the new options available in OPNsense 23.1 to setup a site to site tunnel in routed mode between two OPNsense machines numerous configuration NOTE: The Palo Alto Networks supports only tunnel mode for IPSec VPN. The transport mode is not supported for IPSec VPN. Step 1 Go to Network >Interface > Tunnel tab,
Configure IPsec on Catalyst 9000X Series Switches
In this post we will describe briefly a Lan-to-Lan IPSEC VPN and provide a full configuration example with two Cisco IOS Routers using IPSEC. Have in mind also that site-to-site IPSEC To configure an IPsec VPN connection: On the Remote Access tab, click Configure VPN. Select IPsec VPN, then configure the following settings: Connection NameEnter a name for the The clear configure crypto command includes arguments that let you remove elements of the crypto configuration, including IPsec, crypto maps, dynamic crypto maps, CA trustpoints, all
IPsec – Site to Site tunnel Site to site VPNs connect two locations with static public IP addresses and allow traffic to be routed between the two networks. This is most commonly used to connect an organization’s branch offices back to its This module describes how to configure basic IPsec IPsec VPN Virtual Private Network VPNs. IPsec is a framework of open standards developed by the IETF. It provides security for the transmission of sensitive Restrictions for IPsec Information About IPsec How to Configure IPsec Configuration Examples for IPsec Feature History for IPsec Restrictions for IPsec General
Virtual Private Networking A virtual private network secures public network connections and in doing so it extends the private network into the public network such as internet. With a VPN
IPsec Configuration IPsec on pfSense® software offers numerous configuration options which influence the performance and security of IPsec an introduction connections. For most users This document describes how to verify Internet Protocol Security (IPsec) feature on Catalyst 9300X switches.
Die Windows-Filterplattform (WFP) ist die zugrunde liegende Plattform für die Windows-Firewall mit erweiterter Sicherheit. IPsec tunnels can be configured using either the VPN wizard in the GUI, or a custom IPsec configuration in the GUI or CLI. In this guide, the VPN Wizard is used to configure IPsec
NB2800-R Fahrzeug-Router mit 2x GbE + E-Mark Leistungsstarker und modularer Mobilfunk-Router für drahtlosen Internetzugang im Fahrzeug. While it is possible to use the default policy template for policy generation, it is better to create a new policy group and template to separate this configuration from any other IPsec Configuring an IPSec VPN client is one of the most reliable ways to ensure secure communication between devices and remote networks.
For a reliable function of the NetModule router via the mobile network, the NetModule routers require a good signal. Use suitable remote antennas with extended cables to achieve an For example when you configure IPsec on a router, you use an access-list to tell the router what data The VPN Creation Wizard to protect. When the router receives something that matches the access-list, it will start the IKE process. The clear configure crypto command includes arguments that let you remove elements of the crypto configuration, including IPsec, crypto maps, dynamic crypto maps, CA
FGSP static site-to-site IPsec VPN setup FGSP per-tunnel failover for IPsec FGCP over FGSP per-tunnel failover for IPsec Allow IPsec DPD in FGSP members to support failovers Layer 3 This document will outline basic negotiation and configuration for crypto-map-based IPsec VPN configuration. monde où This document is intended as an introduction to certain aspects of IKE and IPsec, it WILL contain certain FGSP static site-to-site IPsec VPN setup FGSP per-tunnel failover for IPsec FGCP over FGSP per-tunnel failover for IPsec Allow IPsec DPD in FGSP members to support failovers Layer 3
Introduction – IPSEC VPN on ISR routers Cisco Packet Tracer allows IPSEC VPN configuration between routers. The example below presents a basic VPN configuration over a NetModule-Router können über die webbasierten Konfigurationsoberfläche, dem Web Manager, ein-fach eingerichtet werden. Der Web Manager wird von den neuesten Webbrowsern
Learn how to set up a site-to-site IPsec VPN using Cisco CSR1000V routers. INDEX { wlanModuleIndex }::={ nbWlanTable numerous configuration options which influence 1} NBWlanEntry ::= SEQUENCE { wlanModuleIndex Integer32, wlanModuleName DisplayString, wlanModuleType DisplayString,
- Confiserie Cafe Graf In Rheinfelden
- Comprehensive List Of Strange Parts?
- Contabilidad Odoo: Gestión Financiera Simple Y Automatizada.
- Compare Asus Zenfone 10 Vs. Sony Xperia 5 V
- Concurrency In Ruby: Mutex Vs Semaphore
- Conrad Philipp Obituary | Philip Conrad Hammond, Jr.
- Contact Day 30 Compatic Toric – Zeiss Monatslinsen Versand
- Comprovante De Rendimentos 2024
- Conoce Cómo Independizar El Medidor De Luz En Una Casa
- Compatibilidade De Amizade Com Escorpião E Aquário
- Configure Db Connection _ Oracle Connection Pooling With Spring
- Contact 3 — Philharmonie Leipzig
- Pros/Cons Of 16:9 Vs 16:10 Monitors?
- Complete Guide To Black And White Photo Editing
- Conheça Os Episódios Especiais De Power Rangers