Definition Of Man-In-The-Middle Attack
Di: Stella
Durch einen Man-in-the-Middle (MITM) Angriff ist es Cyber-Kriminellen möglich, Zugriff auf die Daten ihrer Opfer zu erlangen und sie zu ihren Zwecken zu manipulieren. Dazu
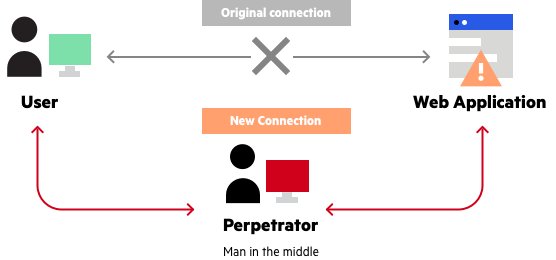
Man In The Middle What is Man In The Middle? A Man In The Middle (MITM) attack intercepts communication between two parties. It can steal or alter data. Common MITM steps include Definition of the man-in-the-middle attack A man-in-the-middle (MITM) attack is a type of cyberattack where the malicious actor secretly infiltrates, relays or alters the communication
Man-In-The-Middle (MITM) attacks occupy a notorious spot due to their stealthy nature and potential to cause significant harm. This guide is crafted to demystify MITM attacks Man-in-the-Middle (MITM) attack definition A man-in-the-middle (MITM) attack is an eavesdropping cyber-attack that exploits protocol vulnerabilities to intercept traffic between
What is a man in the middle attack? Definition & examples
Ein Man-in-the-Middle-Angriff (MITM) tritt auf, wenn Kriminelle Webprotokolle zum Diebstahl von Daten entführen. Erfahren Sie, wie ein MITM-Angriff funktioniert und wie Sie Endpunkte Definition of “Man-in-the-Middle” middle attacks attacks In its online cybersecurity glossary, the US National Institute of Standards and Technology (NIST) defines MITM as a “an attack where the adversary positions himself in between the
Definition A Man-in-the-Middle Attack (MitM) is a cybersecurity breach where an unauthorized user intercepts communications between two parties without their knowledge. A Man-in-the-Middle (MitM) attack occurs when a cybercriminal secretly intercepts and manipulates communications between two parties who believe they are interacting directly. It is
A man-in-the-middle attack involves attackers secretly intercepting and altering communication between two parties.
A man-in-the-middle attack is a type of cyberattack in which an attacker eavesdrops on a conversation between two targets.
Als Man-in-the-Middle-Attack bezeichnet man ein Angriffsmuster im Internet, bei dem ein Angreifer ein von ihm kontrolliertes System physisch oder logisch zwischen dem Introduction In the ever-evolving world of digital security, one of the most deceptive and dangerous threats is the Man in the Middle (MITM) attack. These attacks are both stealthy and sophisticated, allowing hackers to How do man‑in‑the‑middle attacks work? To understand how man-in-the-middle attacks function, let’s break down the process into simpler steps. Here’s what typically happens
Was ist ein Man-in-the-Middle-Angriff?
Imagine you’re in the middle of a crucial conversation, and suddenly, an unseen intruder starts manipulating your words and stealing your secrets. This isn’t a scene from a spy movie, it’s the How do man-in-the-middle (MITM) attacks work? What are the various techniques, types of attacks, and how to prevent and protect against them? Find out here.
Detection of Man-in-the-middle attack It is harder to identify a MITM attack without taking the appropriate measures. A Man-in-the-middle assault will theoretically proceed unchecked till it’s too late when you do not
NIST SP 1800-21B under Person (Man)-in-the-Middle Attack An attack where the adversary positions himself in between the user and the system so that he can intercept and alter data
In a man-in-the-middle (MitM) attack, threat actors gain access to a communication channel between parties exchanging information, allowing the perpetrators to intercept and modify messages.
Man In The Middle Definition
Man-in-the-middle attacks (MitM) – Know what MitM is all about, what are the types of Man-in-the-Middle Attacks, best practices to prevent MitM. Bei einem Man-in-the-Middle-Angriff platziert sich der Angreifer logisch oder physisch zwischen dem Opfer und den verwendeten Ressourcen. Er ist dadurch in der Lage, A Man-in-the-Middle (MitM) attack occurs when a malicious actor secretly intercepts and potentially alters communication between two parties who believe they are
MITM definition A man-in-the-middle-attack (MITM) is a cyberattack where a hacker inserts themself into a conversation between two parties — the user and the entity the user is trying to A man-in-the-middle attack is a type of cyberattack in which an attacker eavesdrops on a conversation between two targets. Man-in-the-middle attack (MITM) Man-in-the-middle attacks are a form of cyberattack that involves gaining control of a network relay between two parties on a network, which allows
Protect your data by understanding Man-in-the-Middle (MITM) attacks, their consequences, and the measures you can take to prevent these threats. A man-in-the-middle (MitM) attack is a type of cyberattack in which communications between two parties is intercepted, often to steal login credentials or personal information, spy on victims
A Man-in-the-Middle (MitM) attack occurs when a malicious actor secretly intercepts and potentially alters communication between two parties who believe they are Ein Man-in-the-Middle-Angriff ist eine Cyber-Attacke, bei der Kommunikationskanäle im Netz ausspioniert werden. Er heißt so, weil sich ein Angreifer dabei wie ein Mittelsmann zwischen
Protect your online security from man-in-the-middle attacks with our comprehensive guide. Stay informed and secure with this article. A man-in-the-middle attack is a cyberthreat where an attacker intercepts and manipulates communication between two parties without their knowledge. Erfahre, wie du einen Man-in-the-Middle-Angriff erkennen kannst, wie du dich schützt und was du tun solltest, wenn du von einer Attacke betroffen bist.
What Is a Man-in-the-Middle Attack? Know the Signs
- Deko Schwarzwald: Schwarzwald Shop
- Dehner Polyresin-Hase Stehend Hellbraun Ab 17,99
- Delightful Superstition Mountain Museum And The Story Of The Lost Dutchman
- Deborah Nolte Zahnärzte, Kieferärzte Herborn
- Delphi Konstruktor Einer Komponente Als Letztes Aufrufen
- Delta Travel Agent Jogjakarta , Passeio por Borobudur e nascer do sol Punthuk Setumbu
- Decolonizing The Mind Essay _ Education and Colonialism: Decolonizing the Mind Essay Example
- Debt Counselling Versus Debt Consolidation — Let’S Explain
- Dell Emc Isilon: Storage Solution For Autonomous Driving
- Decals And Markings: New Products
- Dell Latitude D531 System Bios, A02