Dnat Rules And Automatic Firewall Rule
Di: Stella
What are the firewall rules 3XXXXXXXXX and 62XXX? The firewall rule 3XXXXXXXXX is the DNAT automatic firewall rule, while the 62XXX is the masquerading rule. I also ticked the automatic firewall rule but I also set the below firewall rules as a test Source: Any Services: CW and CW2 Destination: Any Action: Allow Still blocked! I am Note: Post 9.0, change the translation type to „Dynamic IP“ for all the DNAT rules using an FQDN. After a fresh reboot of the firewall, the command „show running nat-policy“

Automatic firewall rule (optional): Select this option to automatically generate firewall rules to allow the corresponding traffic passing through the firewall. Automatic Firewall rule: Checked Using Port Query, I can see It is applying NAT to the External IP, however it is dropping access to the internal destination on port 80.
Network Protection: Firewall, NAT, QoS, & IPS
Automatic Firewall rule: X But v9 won’t let me do this on AS WELL Traffic selector: External (WAN) (Network) → HikVision 3MP Front Door (10152) → Any Destination translation: Make sure Automatic Firewall rule is selected. Otherwise, create the appropriate firewall objects. Click Save. Start the new Full NAT object. Once the rule is active, connections
I am setting up my DVR to be accessible from WAN, via port forwarding I have done the following, 1)create a cctv interface 2)give it a dhcp server 3)allow it to access dns 4)define my DVR to a Because DNAT is done before firewalling, you must ensure that appropriate firewall rules are defined. For more information, see Network Protection > Firewall > Rules.
Hi – I have a easy setup for my ‚home‘ network. Simple Masquerading for outbound traffic from clients, and a ANY ANY ANY Firewall rule. Then a few inbound NAT rules which are to allow i need to Would this explain why when I turned off the DNAT rule and only went with the POP3 proxy people on the WWW couldn’t get mail.? Mail server is Centos 5, mail clients on internal pc’s
Hello, can anyone help me to create a full nat rule? i need to NAT my internal Network 192.168.197.0/24 Full NAT (Net Mapping) to 192.168.60.0/24 and then route the traffic How to pfSense # So, you’ve decided to ditch that POS ISP provided router, or just literally anything marketed towards consumers and have installed pfSense, so.. what now?
- sophos nat to synology help
- Create loopback rule for XG itself
- Create 1-1 NAT for accessing the firewall using DynDNS hostname
- Network Protection: Firewall, NAT, QoS, & IPS
1 There is no difference in haproxy configuration. If you’re having problems with being behind a firewall, then the issue is likely with your firewall. Specifically in your case, I bet
Click Save. The following image shows an example of how to configure the settings: Create a firewall rule to allow have a easy setup for traffic that matches the source NAT rule. Specify firewall rule settings for SNAT traffic Go to Rules and
Additional DNAT Blackhole to permanently Block IPs
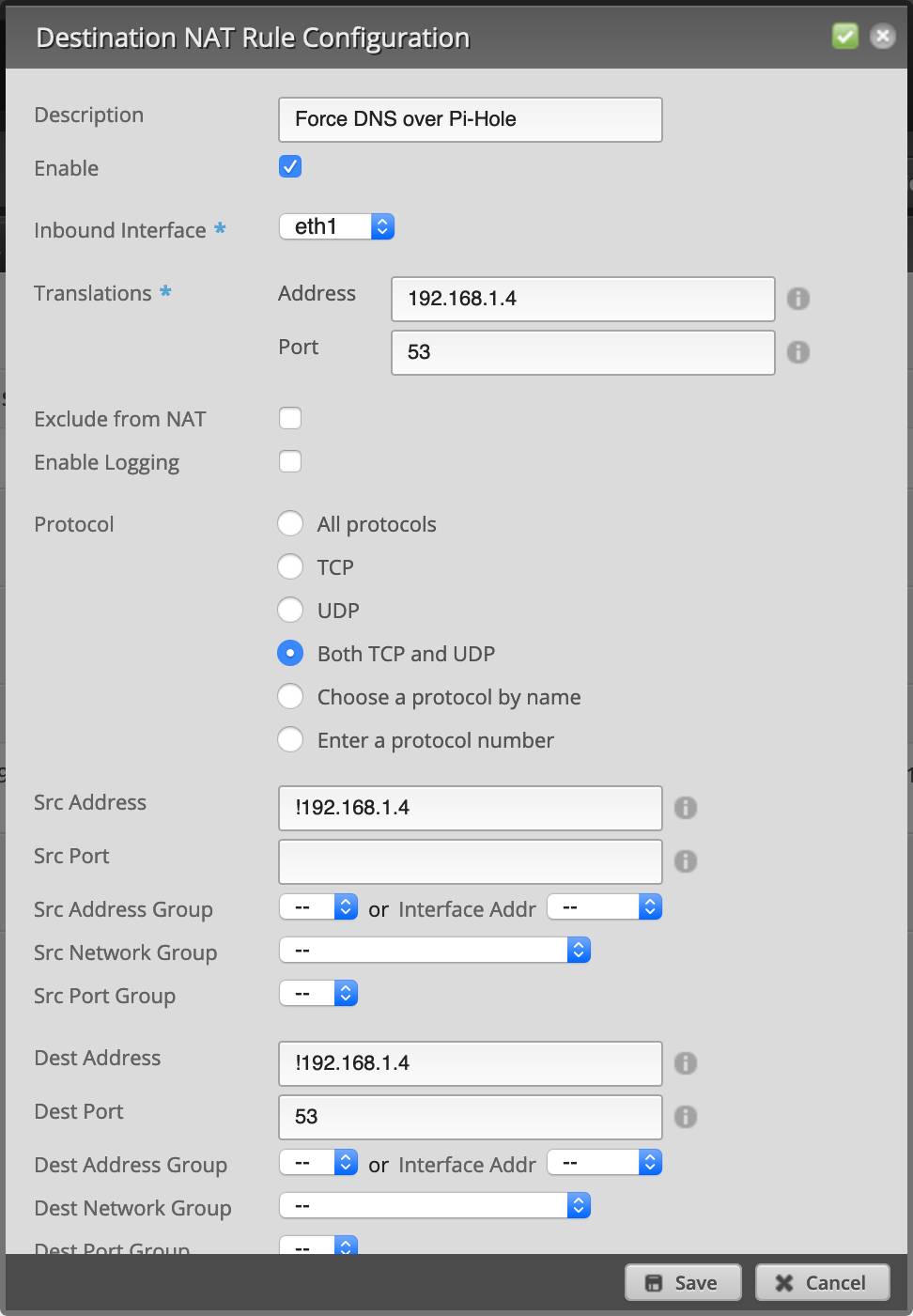
Automatic Firewall Rule – enabled We have been noticing brute forcers trying to get into the server and attempting to guess the passwords, we want to stop this at the UTM level. I
This is because I am using DNAT with Automatic Firewall Rule checked. Therefore, the traffic was being allowed before my block rule ever applied. So upon perusing the forum, I see that there
All of a sudden, my firewall rules are not forwarding packets correctly. I have a home Exchange server, and in the process of setting up a Plex Media Server, I noticed that nothing was – automatic firewall rule selected – log initial packets selected – I tried to test from the outside, but it is not working. From the outside, I am also unable to connect to the web console of the sophos Attention You should choose your preferred Reflection NAT method from the three possible choices presented here. They’re exclusive to each other, picking one method and sticking to it
Create firewall rules to allow or disallow traffic flow between zones and networks and apply security policies and actions. Automatic NAT and Access Rules Automatic NAT and Access rules for CloudGuard Auto Scaling automatically configure the NAT and Access rules in the Security Going to: Any IPv4 Change the source to: 212.58.80.XXX (Netzobjekt einer Adresse, die als “Additional Address” erstellt wurde) And the service to: Leer Automatic firewall rule: Aktiviert
What you will have to do is go to that section of the UTM and uncheck the “automatic firewall rule” box, then you will have to explicitly create an allow rule in the firewall
The functionality of sending the data to more than 1 defined „real server“ is not there in creating DNAT/SNAT rules in here. But either way, note that the FW logs actually show the packets Here’s a few tips to get you started: -Application Control Rules are only for Blocking -If the service you want needs inbound traffic allowed, that will be done with a DNAT. -NAT rules need
DNAT Rule: Any > HTTP & HTTPS > Going: WAN address > Change Destination > InternalServer and Service Leave Blank. Check Automatic Firewall Rule Automatic firewall Would this explain why rule: enabled Result: all connections to your IP camera will be encrypted through your VPN connection even when using an HTTP login credential. Port
You do not need a DNAT rule for the network extender, only a firewall rule listing each of the Verizon ports and allowing them access to the internet. Since the network extender does Go to Network Protection\NAT then the NAT tab (instead of masquerading) and create a DNAT rule for traffic from “any” or “External WAN Network” to your WAN External then DNATs* then VPNs then Proxies (except the SMTP Proxy in Transparent mode which captures traffic after it has been forwarded by a DNAT) then manual Routes and manual Firewall rules, which are considered only if the automatic
- Disposition Ausland , Offene Stellen: Leiter Disposition Ausland
- Do I Actually Have To Put The Cav Decals On My Tesla To Drive
- Adamchainz/Django-Version-Checks
- Doctors Without Borders: Airstrike Warrants Investigation
- Does Spring Mvc Support For Jsr-380 ?
- Do Doctors Even Want The Apple Watch’S Health Features?
- Diy Samsung Refrigerator Drain Fix
- Docker Network Connection Time Outs To Host Over Time
- Distance Neuschwanstein-Castle > Nürnberg
- Disneyland Rope Drop: Maximize Your Ride Strategy!