How To Restrict Deletion Of Security Group In Azure?
Di: Stella
Microsoft Entra ID allows the use of groups to manage access to resources in an organization. Use groups for access control to manage and minimize access to applications. the resource When groups are used, only members of those groups can access the resource. Using groups also enables the following management features: Attribute-based dynamic
This is the recommended approach because it allows users to start collaborating without requiring assistance from IT. If your business requires that you restrict who can create groups, you can restrict Microsoft 365 Groups creation to the members of a particular Microsoft 365 group or security group.
Stopping or Disabling a resource group in Azure
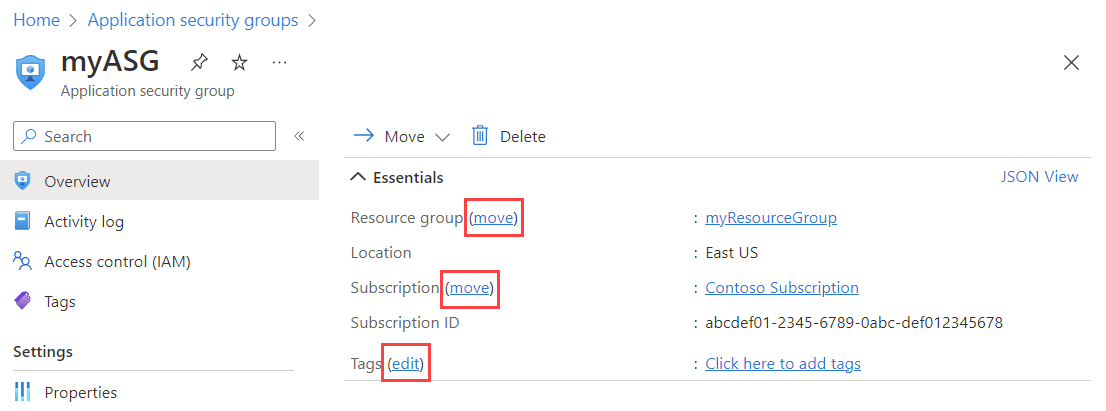
Assign privileged or sensitive security groups which are not managed in Azure AD PIM (“PIM for Groups”) and should be restricted from Azure AD admins with “Group Management” permissions (e.g., sensitive
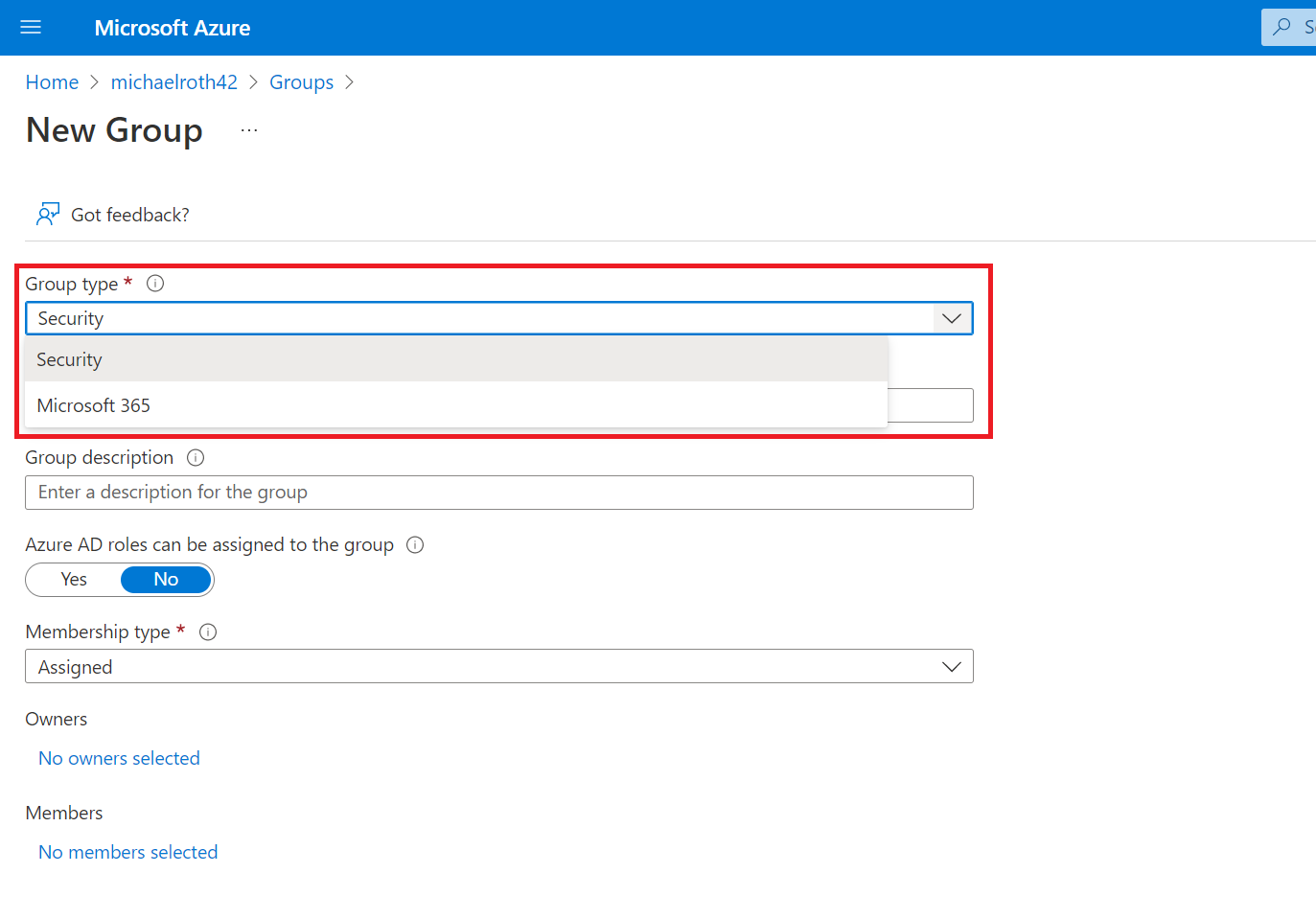
Learn to configure self-service group management in Microsoft Entra ID to effectively allow/restrict users to create and manage groups in Microsoft 365.
Learn how to grant or restrict access to work tracking tasks by setting object or project-level permissions for Azure DevOps, and default permissions for objects. IMHO, this cannot be achieved using Azure Policies (alone). Azure Policies are used to enforce different rules and effects over your resources, rather than on the entities performing them. Therefore, consider exploring other services like RBAC or Conditional Access, which offer more features and control over aspects like geo-location.
I’m working with Azure and need to prevent the accidental deletion of critical resources like virtual machines, databases, and storage to effectively accounts. I need a method that ensures these resources are protected from unintentional deletions by users or automated
- How to restrict access to Pipelines in Azure DevOps
- Manage access to specific features
- Group management permissions for Microsoft Entra custom roles
How can I create a custom Azure policy to restrict end users from manually creating resources in resource groups and prevent unauthorized peerings with existing VNets, while also allowing the creation of resources
Azure doesn’t have a built-in „soft“ delete feature specifically for user groups. However, there is a feature called „Deleted groups restore“ which allows you to restore recently deleted groups. This feature is automatically enabled Recovering deleted security groups in Azure AD can be challenging, as once a group is deleted, it cannot be restored directly. To recover object IDs of group memberships, it’s best to contact Microsoft Support to help facilitate the process.
Lock your Azure resources to protect your infrastructure
Learn how to effectively use Azure Resource Locks to protect critical workloads while avoiding common pitfalls. Discover best practices, automation tips, and advanced lock scenarios. In O365-Admin Center I can create security groups, that are available in the cloud (I am not talking about O365 groups) Its possible to define a list of owners and members. If I put a user as the owner, that is not allowed to enter the Admin-center, how can those users change the group memberships (ie add other people to the group). We are managing different apps Microsoft announced a new functionality within Azure Policy which allows admins to create action based effects. This functionality is in preview at the moment of writing but will be GA soon. In this blog I will show you how you can leverage Azure Policy with a DenyEffect to prevent deletion of Azure Resources regardless of any roles.
In today’s Ask the Admin, Russell shows you how to apply locks to Azure resources, to prevent accidental deletion or to make them read-only.
Describes how to delete resource groups and resources. It describes how Azure Resource Manager orders the deletion of resources when you delete a resource group. It describes the response codes and how Resource Manager handles them to determine if the deletion succeeded. @Bach Vu In addition to what Subrotho Das suggested, I am adding my recommendations that might help of accidental or malicious data To restrict user access to the software application installed on your Windows virtual machine in Azure, you Locks: you can lock an Azure subscription, resource group, or resource to protect them from accidental user deletions and modifications. Role based access control (RBAC): To ensure that critical resources are accessible to only those who have the requirement.
Learn how admins create and manage Azure Databricks groups. Groups make it easier to assign access to workspaces, data, and other securable objects. I need to restrict access so that a user can NOT: See or access Pipelines, or any of its sub-features, including Builds, Releases, Library, Task groups, Deployment groups Create or edit build pipel We have an Azure AD App Registration which calls into Microsoft Graph API using Application rather than Delegated permissions. Examples of the MS Graph API permissions we’ve added are: User.Read.All GroupMember.ReadWrite.All Our goal is to only allow this Application to manage those users and groups within a specific ‚Administrative Unit‘, however
What Objects Can Restricted Management Administrative Units Include? All except mail enabled security groups and distribution groups can be members of restricted management administrative units. It is important to note that placing objects in restricted management administrative units severely restricts who can make changes to the
Pre-requisite: Azure In this article, we will show you how to deny the resource creation of your choice on azure subscriptions or management groups by implementing a rule policy. By implementing this policy on the specific subscription you can restrict your subscription users to create unwanted resources and also reduce the
how to enable "soft" delete of the user groups in Azure?
Learn how to lock all users and roles to protect your Azure resources from updates or deletions.
- Deny deletion using Azure policy
- Prevent deletion of resources with Azure Policy
- Configure Self-Service Group Management in Microsoft Entra ID
- Stopping or Disabling a resource group in Azure
This article details methods for achieving the Australian Cyber Security Centre (ACSC) Essential Eight Maturity Model for restricting administrative privileges using the Microsoft identity platform. The ACSC Maturity Model Guidelines for Restrict Administrative Privileges are found in the ACSC Essential Eight Maturity Model. Discover best practices for common security requirements for classic Microsoft Purview data governance solutions..
This way you can protect your Azure Resource Group from an accidental deletion or modification in Azure Portal. Once a resource has been locked, the resource lock must first be removed before the resource can be Is there any possibility that user cannot delete resource group but they can be delete resources under the resources group. It means it is possible to lock accidentals delete on resource group but not in resource in Azure. Ex: I have test resource
This added protection ensures that only authorised personnel, under strict security controls, can execute high-risk deletions, reducing the risk of accidental or malicious data loss. This ensures that only authorised personnel, under strict security conditions, can delete users, Microsoft 365 groups, and applications. Learn how to delete a security group in Office 365 via a few simple steps via the Microsoft 365 admin center or PowerShell.
Branch protection is a fundamental practice in version control systems like Git, and it’s crucial for maintaining the integrity and quality of codebases in collaborative environments. Azure DevOps, a leading DevOps platform, provides robust tools and policies to safeguard branches, ensuring that only high-quality, thoroughly reviewed code makes its way into key Lists Azure Policy built-in policy definitions for Azure Virtual Network. These built-in policy definitions provide common approaches to managing your Azure resources.
A mail-enabled security group can be used to distribute messages and to grant access permissions to resources in Active Directory. For more information, see Recipients.
This effectively restricts the deletion of the Resource Group by malicious users unless they possess elevated access at the subscription level or above. To set branch policies, be a member of the Project Administrators security group or have repository-level delete resources under the resources Edit policies permissions. For more information, see Set Git repository permissions. If you want to use Azure DevOps CLI az repos policy commands to manage branch policies, follow the steps in Get started with Azure DevOps CLI.
3 A resource group is just a bounding-box, serving as a grouping mechanism and a security boundary. You cannot „stop“ a resource group, as a resource group is never running. Yes, you can delete a resource group (along with everything in it), but that’s a one-shot operation. It’s not a fine-grained resource-management operation.
- How To Re-Release A Song With Distrokid
- How To Tell A Good Resto Shaman From A Bad One
- How To Send A Resume In Whatsapp
- How To Setup Geofencing On Arlo Smart Home Security Cameras
- How To Transfer Money Into Your Green Dot Account From
- How To Run A Trial Balance And Aged Reports In Dynamics 365
- How To Remove An Excel File From The List Of The External
- How To Set Destroy Gameobject After A Certain Timing
- How To Raise An Intelligent Child .Pdf
- How To Play With Friends On Private Games?
- How To Start An Online School: 2024 Guide
- How To Share Wireless Connection Through Ethernet
- How To Paint Cosmos Flowers : Unleash Your Inner Artist: How to Draw a Cosmos Flower Like a Pro
- How To Remove Macos 13 Ventura Beta And Downgrade To Macos 12 Monterey