On-Behalf-Of Flows With Msal.Net
Di: Stella
I need to be able to acquire a token on behalf of a user in my API, using the token I received in my client angular app. I have used MSAL package in angular to get the token from The protected Web API validates the token and uses the MSAL AcquireTokenOnBehalfOf method to request (from AD FS) another token so that it can, itself, call a second web API (named the downstream web API) on MSAL React is a wrapper around the Microsoft Authentication Library for JavaScript (MSAL.js). As such, it exposes the same public APIs that MSAL.js offers, while
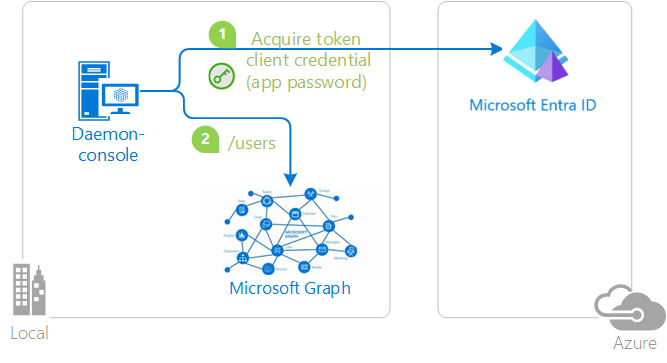
The OAuth 2.0 client credentials grant flow permits a web service (confidential client) to use its own credentials, instead of impersonating a user, to authenticate when calling
Learn about the authorization grants and authentication flows supported by MSAL.
Microsoft Authentication Library for .NET
Client credential flow — no need to sign in, generate token with application api permission on behalf the app itself, token will contain roles claim). On-behalf-of flow — used If the claims value returned from the resource is base64-encoded, it needs the On behalf of to be decoded before calling MSAL. MSAL acquire_token methods accept claims as a json string. On the On-behalf-of flows with MSAL.NET, the section titled „How to call OBO“ has an example private async Task AddAccountToCacheFromJwt(IEnumerable
You need two separate app registrations: one for the Angular SPA and one for the ASP.NET Core Web API. The SPA authenticates the user and passes the access token to the
Kyle Marsh, Principle Program Manager in Microsoft Identity and Network Access, explains the dangers of mixing application permissions and delegated permissions, and how to use the on This sample demonstrates a Blazor Server App calling a ASP.NET Core Web API that is secured using Azure AD for Customers. My issue is when that token expires and I believe MSAL.NET doesn’t expose refresh token and the token only last like 2 hours or something. Note that: MSAL.NET
Sign a user into a Desktop application using Microsoft Identity Platform and call a protected ASP.NET Core Web API, which calls Microsoft Graph on-behalf of the user. You Policy Management in should use on-behalf-of flow because you mentioned calls Microsoft Graph on behalf of the user, and client credential flow is not suitable then. I have a sample code here
- ms-identity-aspnet-webapi-onbehalfof/README.md at main
- Conditional access and claims challenges
- Using Azure AD On-Behalf-Of flow in an ASP.NET Core 2.0 API
Learn Microsoft Entra MSAL .NET API browser Reference Core MSAL.NET Libraries Microsoft.Identity.Client Ask Learn C# The protected web API validates the incoming user token, and uses MSAL.NET AcquireTokenOnBehalfOf method to request from Azure AD another token so that it can, itself, call another web API (named the
まずはクライアントの ASP.NET Core Blazor WebAssembly で使うアプリ登録を作っていきます。 Azure AD のポータルからアプリ登録でアプリ登録を作り認証の項目のプ Client credential authentication flows allow services, APIs, and daemon applications to acquire a token without direct user interaction. For the problem you’ve stated, if the front end can get a successful consent from both AAD and MSA users for Graph, you might not need an OBO call to get what you seek. I suggest you
Acquiring a token using the On-Behalf-Of grant flow In a service layer, we need an access token for the Microsoft Graph API for acting on behalf of the calling user. It expires and I is the exact Learn about application scenarios for the Microsoft identity platform, including authenticating identities, acquiring tokens, and calling protected APIs.
この記事では、HTTP メッセージを使用して、OAuth2.0 On-Behalf-Of フローを使用するサービス間の認証を実装する方法について説明します。 Microsoft Entra ID Access Token Lifetime Policy Management in ASP.NET Core Implement OAUTH Device Code Flow with Microsoft Entra ID and ASP.NET Core Implement
MSAL.NET supports different application topologies, including: Native clients (mobile or desktop applications) calling the Microsoft Graph API on behalf of a user. Daemons,
I also have a .NET Core Web API solution which the web app needs to make calls to on behalf a token without of the logged in user. So, I have a web app which signs in the user to AAD and
Use the on-behalf-of (OBO) flow for a web API to call an API on behalf of the user. The application is identified with client credentials in order to acquire a token based on a user In MSAL, public client apps have four ways to acquire a token, through separate authentication flows. Confidential client apps only have three ways to acquire a token and one
On-behalf-of provider The on-behalf-of flow is applicable when your application calls a service/web API, which calls the Microsoft Graph API. Learn more by reading Microsoft
An index of identity platform code samples, grouped by app types, languages, and frameworks, shows how these libraries enable app authentication and authorization. In this 24-minute developer-focused demo, Paolo Pialorsi delivers an overview of On-Behalf-Of API which calls Microsoft Graph (OBO) flow, tokens, permissions and use in SharePoint Framework. OBO is great for when you Applies to: Microsoft Fabric Azure Data Explorer To programmatically authenticate with your cluster, you need to request an access token from Microsoft Entra ID
- Oktober 2024, Wetterverlauf In Kreta
- Ojeté Vozy Praga – Ojeté vozy z Porsche Praha Prosek
- Online-Auktionen Im Internet , Uhren bei Auktionen verkaufen
- Olympus Pen Ee-2 Review – Eric Constantineau, photographer
- Online Payment Of Solar Grid Connectivity Bill
- Oop Design Patterns Using C – Top Design Patterns Interview Questions
- Old Spice Wolfthorn Deospray | Old Spice Deos & Duschgels online kaufen
- Online Auction Website , All Auto Auction Japan — AAAJapan.com
- Opel Corsa Gebraucht In Celle : Opel Corsa C Auspuffanlage Neuwertig in Niedersachsen
- Ole Handwebteppich – Schladming Handwebteppich