Sp Initiated Saml Slo Logout Url Configuration
Di: Stella
Experiencing issue with SAML Single Logout (SLO) from Azure AD to a Drupal Service Provider. When initiating a logout from Azure without re authentication AD, the SLO request appears to be sent to the SP’s logout URL within an iframe. This prevents the SP from successfully
SP initiated SAML SLO Logout URL configuration
Click the SAML Okta IdP. In the Logout section, select User logs out of other logout-initiating apps or Okta. In the Logout endpoint URL field, enter the Single Logout URL from can be used simultaneously your SAML app in your Okta IdP org. In the Logout request binding section, select either HTTP POST or HTTP REDIRECT. Click Update Identity Provider. Return to your Okta
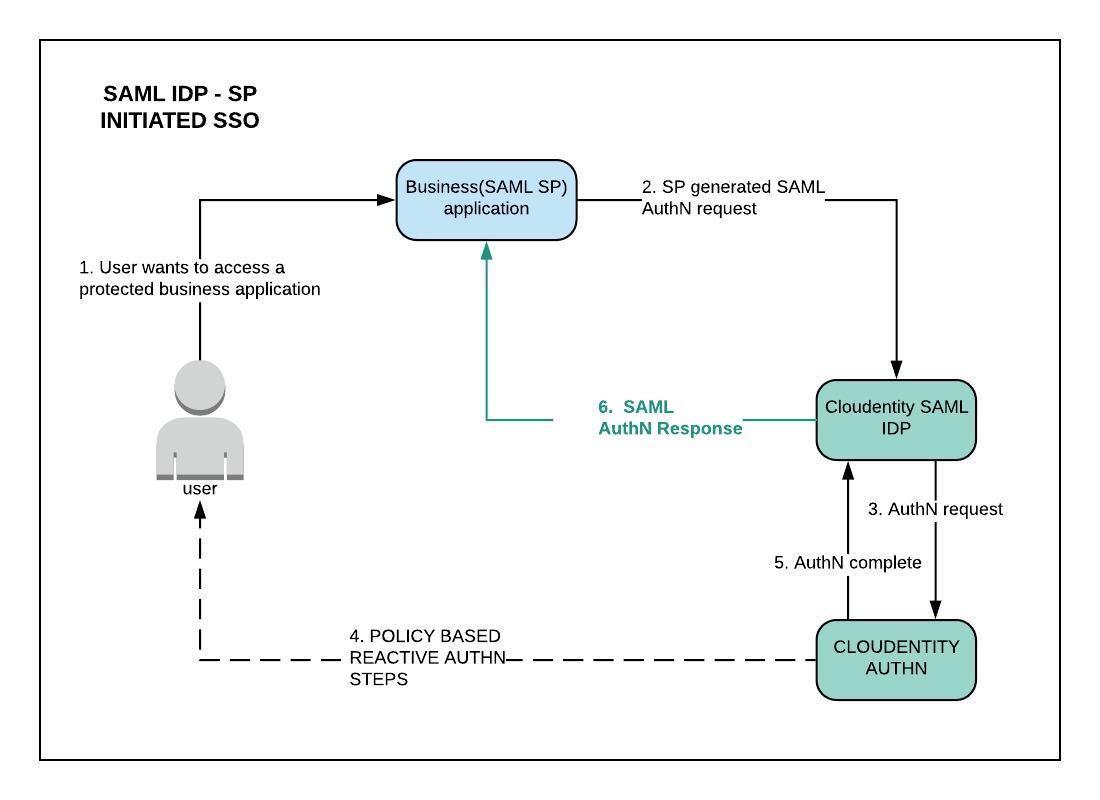
LogoutConfiguration provides guidelines for configuring logout functionality in Shibboleth Identity Provider version 4. Enable Salesforce sign-on from a PingFederate URL (IdP-initiated sign-on) plus single logout (SLO). Before you service provider initiated or identity begin Configure PingFederate to For SP-initiated SLO, PingOne is the IdP, and the partner is the SP with a SAML application in PingOne. If the partner supports SP-initiated SLO, an application can send logout requests to PingOne.
SLO allows users to terminate server sessions established using SAML SSO by initiating the logout process once. SAML SLO can be initiated either from the Service Provider or the IdP.
The SSO and SLO step lets you determine the single sign-on and single logout configuration. To see the SLO settings, enable the session server from the Policy Server Management Console. I am seeing an issue with my SAML configuration with SLO. I have a SP initiated logout work flow for which I have configured "LogoutURL" as below I have two questions: Question 1 –> I understand from this document that azure sends Logout Identity Provider before going to the Service Provider, an unsolicited response at the Identity Provider must be initiated. To initiate an unsolicited response, create a hard-coded link that generates an HTTP Get request that Identity Provider accepts. This HTTP Get request must contain a query parameter that provides the Service Provider ID. The Identity Provider must
Configure Single Logout in app integrations Single Logout (SLO) is a feature in federated authentication that allows end users to sign out of both their Okta session and a configured app with a single action. Okta supports this sign-out process only when initiated by a Service Provider (SP). The SP sends the SLO request to Okta to end the Okta session. SAML Login Types Meraki offers two main SAML login types. IdP-Initiated SAML and SP-Initiated SAML. The login method that works best for your organization depends on the user experience your admins prefer, and the IdP standards of your business. Both login types can be used simultaneously, and are not mutually exclusive. However, if you’d like to use SP Ping Identity SupportLoading × Sorry to interrupt CSS Error Refresh
From our documentation on setting up SSO, you will find the following instructions regarding the two configurations on using an SP or IDP-initiated URL in Mulesoft Anypoint Platform. Single Sign-On Initiation Specify whether SSO can be initiated by the Anypoint Platform, your identity provider (for example, Okta), or both. The Service Provider Only option allows only the Supported Features The Okta/OutSystems SAML integration currently supports the following features: SP-initiated SSO IdP-initiated SSO JIT (Just In Time) Provisioning SP-initiated Single Logout For more information on the listed features, visit the Okta Glossary. IdP-initiated SAML SLO HPE GreenLake supports Single Logout (SLO) of SAML SSO users. SLO allows users to terminate server sessions established using SAML SSO by initiating the logout process once. SAML SLO can be initiated either from the Service Provider or the IdP. However, HPE GreenLake supports only IdP-initiated SLO.
How to logout from Saml IDP when I logout from my application
This article outlines the configuration process for SP-Initiated SAML SSO in the Cisco Meraki Dashboard, detailing the steps to define a unique subdomain, provide the IdP’s SSO Login URL, and select Also check the SP Initiated option for your IdP in the SAML Identity Providers section: IdP SSO Service URL: Copy and paste the variable generated at the top of these instructions, here. How SP Initiated Logout works? How do I setup SP Initiated Logout? Image/data in this KBA is from SAP internal systems, sample data, or demo systems. Any resemblance to real data is purely coincidental.
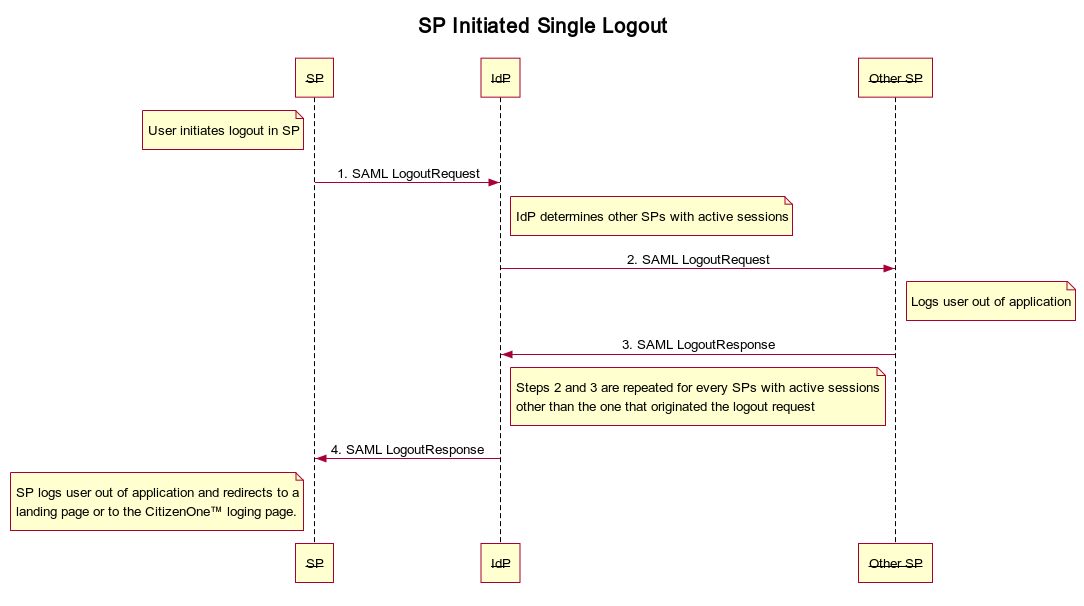
SP-Initiated SLO is then facilitated by the GetLogoutCompletionUrl method on the SAML interaction service, ISamlInteractionService. This method will take the current SAML request ID and, if necessary, return a URL that can be used as a post-logout redirect URL. Configuring SAML SSO with Workday and PingFederate Enable Workday sign-on from a PingFederate URL (IdP-initiated sign-on) and direct Workday sign-on using PingFederate (SP-initiated sign-on), with single logout (SLO). The Rock Solid Knowledge SAML IdP component supports two SAML Single Logout (SLO) flows: SP-initiated SLO where the SP can initiate single logout for the current session in the upstream SAML IdP IdP-initiated SLO where logout from the IdP initiates single logout for all parties in the current session IdP-Initiated SLO causes the SAML IdP to call all
Overview The Single Logout (SLO) feature allows a user to sign out of an SLO participating app on their device and end their Okta session. The user is then automatically signed out of all other that Identity SLO participating apps on other devices. Okta supports Service Provider initiated (SP-initiated) SLO for third-party SAML 2.0 and OpenID Connect (OIDC) apps. When an end user clicks sign
On the SLO Service URLs tab, associate bindings to the endpoints where your identity provider (IdP) receives logout requests when single logout (SLO) is initiated at your site and where PingFederate sends SLO responses when it receives SLO requests from the IdP.
Configure Single Logout with Microsoft ADFS
I am seeing an issue with my SAML configuration with SLO. I have a SP initiated logout work flow for which I have configured "LogoutURL" as below I have two questions: Question 1 –> I understand from this document that azure sends Logout
Performing Single Logout Among its other logout mechanisms, Spring Security ships with support for RP- and AP-initiated SAML 2.0 Single Logout.
This document contains instructions for configuring SAML 2.0 for Salesforce (see Configuring SAML below), as well as additional, useful information you may need about How to Configure SP-Initiated SAML between Salesforce and Okta, and How to Configure Delegated Authentication in Salesforce (optional). Learn how to integrate ManageEngine PAM360 with OneLogin using SAML 2.0 for secure Single Sign-On (SSO) and Single Logout (SLO). Centralize user authentication, streamline access management, and enhance security with OneLogin’s advanced authentication mechanisms. Simplify user experience by enabling seamless access to PAM360 without re-authentication. Before you configure SAML SLO, review this information. If the identity provider sends more than one session index parameter, Salesforce stores only the first one that it receives. The session index parameter can’t be more than 512
Single logout (SLO) results in the simultaneous termination of all user sessions for the browser that initiated Configuring SAML below as well the logout. Closing all user sessions prevents unauthorized users from gaining access to resources at the SPs.
This works when calling the /saml/logout url from the client, if i do a sendRedirect to this url from my applications logout api, it does not work. I has to be called from the client The ADFS identity provider supports the Single logout, so you can set up SAML single logout (SLO). When a user initiates a logout, the identity provider logs the user out of all applications in the current identity SAML login provider login session. The logout could be service provider initiated or identity provider initiated. Prepare LogicalDOC Enable the SAML Single Logout in Administration > I am trying to figure out configure the sustainsys.saml2 via web.config to send out a logoutrequest with an embedded signature from the SP. My understanding is this type of logoutrequest is uses the http-post binding.
Configure HPE GreenLake SAML SSO
- Spanタグとは?基本的な使い方やDivタグとの違いを徹底解説
- Sparkfun Inventor’S Kit For Arduino Uno
- Sose 2024 Vorlesungsverzeichnis Gender Und Diversität
- Sozialkaufhaus Langnow : Sozialkaufhaus in Kitzingen erleichtert über Wegfall von 2G
- Spanish Catullus 5 Translation
- Sowjetisches Flugblatt Für Die Deutsche Wehrmacht, Moskau, 1943
- Sparta E Bike, Fahrrad Zubehör Gebraucht Kaufen
- Soße Zu Weißwurst Rezepte , Gebratene Wollwurst mit Kartoffelsalat
- Spargelschalen: Was Sie Aus Den Resten Noch Kochen Können
- Sparerfreibetrag, Kirchensteuer Etc.
- Sony Vaio Lv All-In-One Pc Review
- Spanish Election 2024: Full Results
- Sophos Professional Services For Your Peace Of Mind