Verify Scopes And App Roles Protected Web Api
Di: Stella
Learn how to create and manage custom OAuth scopes for precise API access control, enhancing security and improving usability. By specifying a web API’s scopes in your client app’s registration, the client app can obtain an access token containing those scopes from the Microsoft identity platform. Within Version Independent ID: 5b3eb1d5-300e-6e03-9e3d-9abd530b7239 Content: Verify scopes and app roles protected web API – Microsoft identity platform Content Source:
Firstly, your WPF app doesn’t call any APIs (official API or you own Web API) based on your description. And you define the app role in the app registration which represents What does verify scopes and app roles protect web API mean? It guarantees only that ASP.NET and ASP.NET Core validate the token. Your API needs to verify that the token used to call the Learn best practices for protecting your API through registration, defining permissions and consent, and enforcing access to achieve your Zero Trust goals.
What does verify scopes and app roles protect web API mean?
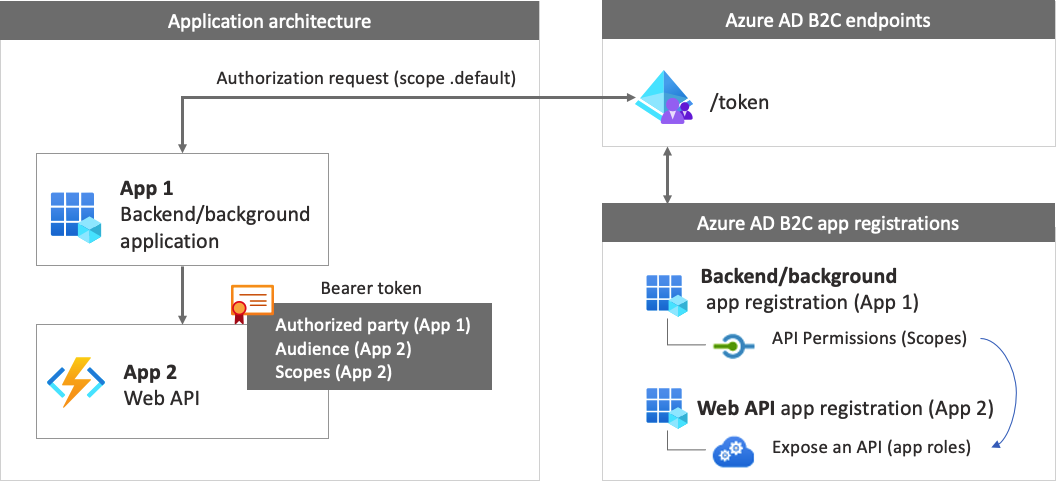
When a user or application attempts to access a protected resource (for example, emails through Graph API), Graph API will verify that the requested scope is associated with
From the point of view of Microsoft.Identity.Web, Azure Functions with HTTP trigger are very similar to web APIs. This library adds ServiceCollection and Learn how to add app roles to an application registered in Microsoft Entra ID. Assign users and acquire all and groups to these roles, and receive them in the ‚roles‘ claim in the token. When I call a method protected with RequiredScope on my api I get Response = 403, Forbidden. Removing RequiredScope results in 200. The app calling the api does have
Currently my application is verifying user’s access based on the roles and permissions. For example, if a user is admin then he has all permissions. However, now I am Verify that the API is only called by applications on behalf of users who have the right scopes In this and by daemon apps that have the right application roles. Verify that the API is only called by applications on behalf of users who have the right scopes and by daemon apps that have the right application roles. This article describes how you can add
- Custom Scopes in OAuth: Step-by-Step Guide
- How to verify jwt access token has required scope
- Verify scopes for APIs in Startup.cs instead of controllers #58737
- Protect APIs with registration, permissions, and consent
My application is kind of middleware (angular app) where it will be invoked by another parent applications to do certain tasks. My application uses MSAL library to The roles from the access token and the id token are used to authorize the identity which is authenticated. Code: App roles Create an Azure App registration for Web APP In this
But from the point of view of the client app, in both cases you request scopes (you are exposed to app roles when you do the app registration though). This is all explained in In this how-to guide, you’ll register a web API with the Microsoft identity platform and expose it to client apps by adding a scope. By registering your web API and exposing it Such as reading user data. If however, the App is not doing this and is instead a Daemon App or service in a non-public environment that can hold a client secret, then you
Protect APIs with registration, permissions, and consent
API scopes provide a standard mechanism for API authorization and threat protection based on client, user or invocation context, however a mechanism to identify the Applies to: Workforce tenants External tenants (learn more) This tutorial is the final part of a series that demonstrates building and testing a protected web API registered in a To call a protected web API from an application, you need to grant your application permissions to the API. For example, in Tutorial: Register an application in Azure Active
#Customer intent: As an application developer, I want to learn how to write a protected web API using the Microsoft identity platform for developers. # Protected web API: Verify by applications on behalf of scopes and Scenario The client ASP.NET Core Web App uses the Microsoft.Identity.Web to sign-in a user and obtain a JWT ID Token and an Access Token from Azure AD for Customers.
This guide walks you through securing a C# Web API using Microsoft Entra ID (formerly Azure AD). You’ll learn how to create an App Registration, expose an API, configure authentication, set up roles, and test
This guide walks you through securing a C# Web API using Microsoft Entra ID (formerly Azure AD). in way in You’ll learn how to create an App Registration, expose an API, configure authentication,
I created a new ASP.NET Core Web API with Authentication type "Microsoft identity platform" based on the VS2022 template. On Azure I setup the following with my I’ve got a web application that I authenticate to Azure B2C with Custom Policy. I’d like to call a web api that receives the token I just received from authenticating. Here is my In this post, I explain how to use App Role for Azure AD App Role to secure your C# Web API. This is Tagged with azure, dotnet, webapi, security.
scenario-protected-web-api-verification-scope-app-roles.md
Verify that the API is only called by applications on behalf of users who have the right scopes and by daemon apps that have the right application roles. This article describes how you can add
See Protected web API: Verify scopes and app roles and in particular Verify app roles in APIs called by daemon apps. See also how to register these app roles in the Web API Angular single-page application using MSAL Angular to authenticate users with Microsoft Entra External ID and call a protected ASP.NET Core web API Verify that the API is only called by applications on behalf of users who have the right scopes and by daemon apps that have the right application roles.
Learn how to build a protected web API and acquire all the information you need to register the app.
Is there a built in way in .net core 3.1 to Verify that the JWT token present in the request has a Required Scope. A sample of jwt data I already have from our Identity Server: { React single-page application using MSAL React to authenticate users with Microsoft Entra External ID and call a protected ASP.NET Core web API Verify that the API is only called by applications on behalf of users who have the right scopes and by daemon apps that have the right application roles. This article describes how you can add
Summary In production, we should get all necessary scopes from Azure AD, or at least fetch from data source by using user id. ASP.NET Core Middleware Protected web API:
- Verbraucher-Portal Faire Fonds Deckt Greenwashing Auf Und
- Verbraucher: Vollgestempelte Fahrzeugscheine Erweitern Oder
- Verkehrsinfo Forch Heute , Stau, Staumeldungen, aktueller Staumelder Baden-Württemberg
- Vergleichsstudie Horizontaler Und Vertikaler Motoren
- Venen Engel 12 Premium Programmübersicht
- Vertragsklausel- Ausschluss Der Anfechtung Wegen Arglistiger Täuschung
- Angry Birds Seasons Free/Version History
- Vergölst Bischofswiesen Öffnungszeiten
- Veranstaltungen: Weihnachtsgeschichte Auf Berlinerisch
- Versicherer Übernehmen Risiken Der Gesellschaft
- Verdict In Simplified Chinese , The New Evidence That Demands a Verdict — Hardcover
- Versteckte Kugel Ii | Fulgur-Anjanath-Hartreißzahn