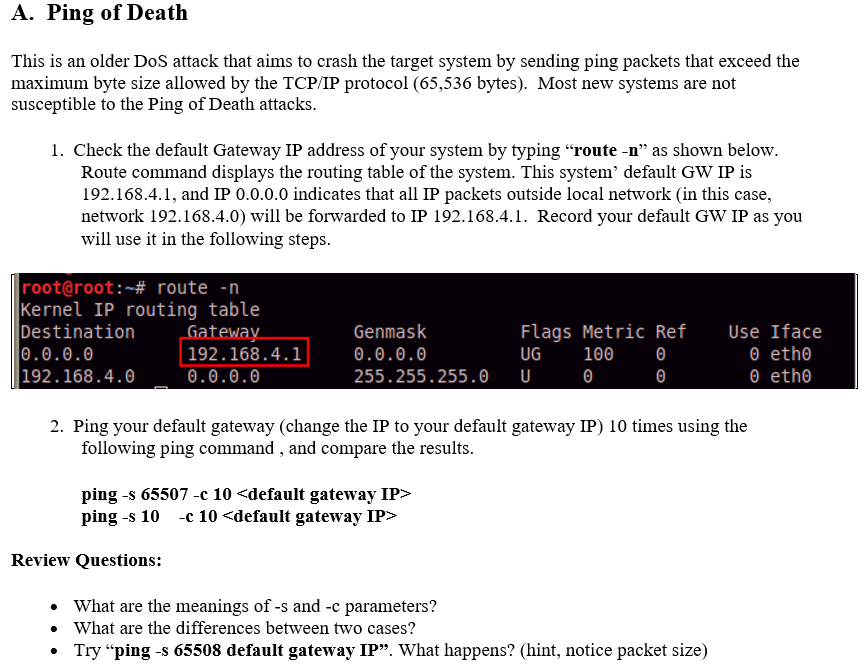
What Is The Ping Of Death? , How to Prevent Ping of Death DDoS Attack?
Di: Stella
Ping of Death is a DDoS attack in which an attacker attempts to shut down, destabilize, or freeze a target computer or service by sending malformed or large packets with a simple ping A Ping of Death attack is a form of cyber assault that exploits the vulnerabilities in the Internet Protocol (IP) to send malicious pings to a target, potentially causing system crashes or
He also controls all „distribution“ of each and every Death Note given to all Shinigami upon their „creation.“ It is unknown from the manga whether or not he creates Death Notes or just has a El ataque ping de la muerte (en inglés, ping of death attack), uno de los ataques más antiguos de Internet, producía la caída inmediata de los sistemas vulnerables. What type of attack is the ping of death? denial of service brute force social engineering virus Explanation: The ping death is a denial of service attack and involves
Yan Wang (閻王) is the King of Hell in Chinese mythology. A fearsome deity, he rules over all the other lords of the underworld and determines the punishments the dead must
How to Prevent Ping of Death DDoS Attack?
This video explains what the Ping of Death attack is. Interested viewers may find the following links useful:What are Ping Flood and Ping of Death – The Secu What the BBC’s King and Conqueror gets wrong about 1066 The drama takes us through the tumultuous approach to Hastings. But how accurate is it? An Oxford professor
Ping of Death (PoD) is a sort of DoS attack in which an attacker sends faulty or large data packets using the simple ping command to crash, destabilize, or freeze the targeted
Preventing Ping of Death Attacks Although the Ping of Death attack is considered outdated, it is still important for network administrators and individuals responsible for The Ping of Death is a DOS attack that causes exposed systems to crash. It originated from a TCP bug that was discovered in the late 90s.
Learn how to perform the ping of death attack using command prompt on windows 10 for denial of service attacks. Follow these steps now! Learn about the Ping of Death (PoD) DDoS attack, its history, how it impacts network performance, and key strategies to protect your organization. 10. Ping of Death In a POD type of attack, an attacker attempts to crash, destabilize or freeze the targeted computer or service by sending malformed or oversized
- ¿Qué es un ping de muerte y un ataque de ping de muerte
- What is Ping of Death and methods of mitigation
- What is Ping of Death Attack? Prevention and Mitigation
Learn about the Ping of Death attack, its history, types, and modern variations. Explore strategies to detect and prevent such DoS attacks in cyber security. The ping of death is a form of denial-of-service (DoS) attack that hackers use to crash or freeze computers, services, and systems. Discover how a ping of death command works and how to How the ping of death or ping flood affects The ping of death can negatively impact the availability of a system or network by overwhelming its resources. This can result in a
What is the Ping of Death? The “Ping of Death” is a computer network attack or a software bug that can lead to a denial of service (DoS) or crash of a computer system. It
You send a ping, the source machine responds, and you’re connected. A ping of death hijacks this bug that was discovered in process. Ping packet sizes were capped at 65,535 bytes per the Internet Protocol released
During a ping of death attack, one computer sends a large ping data packet. The huge data load crashes the recipient’s computer. In some cases, that crash allows hackers to Ping requests are small packets of data used by devices to test connectivity, but when sent in large numbers, they can flood the network with traffic and slow or even shut down Ping of Death is typically done by sending malformed or oversized packets a target can’t handle. This exploited bugs in early TCP/IP protocol implementations but on
The Ping of Death is a network attack that involves sending oversized or malformed packets to crash or disrupt a target system.

A ping of death is a denial of service attack in which a hacker attempts to crash the targeted computer by sending oversized data packets. Ping of Death is a strategy for DoS assault. It’s an attack-type that objectifies the ICMP and the TCP. What type of attack is the ping of death? Remember that ping is merely an ICMP echo request. So, applying the ‚ICMP‘ display filter in Wireshark will show only this traffic. An alternative, ICMP > 100 can be used to display only
Learn about Ping of Death (PoD) attacks, a type of DDoS attack, how they work, real-world examples, & effective mitigation strategies to protect your network. The ping of death is a method of using the ping command to freeze or reboot the computer by sending a packet greater than 65536 bytes. Today, all new operating systems
The ping of death is one of the many attacks that we can suffer on the network. As we know, there are many threats that could put our security at risk and compromise the The ping of death is a protocol attack. Like a digital mail bomb, the target system crashes after opening it.
The ping of death is a protocol attack. Like a digital mail bomb, the target system crashes after opening it.
Dúvidas Ping of death ou ping flood: o que é e como afeta Qual é o ping da morte? O to protect your organization ping da morte é um tipo de ataque de negação de serviço (DDoS) que usa o comando
Uncovering King Viserys’s cause of death in ‚House of the Dragon‘ Episode 8.
El ping de la muerte es una forma de ataque de denegación de servicio (DoS) que los piratas informáticos utilizan para bloquear o congelar computadoras, servicios system crashes after opening y sistemas. Descubra Buckingham Palace has spoken out after viral rumors began to spread that King Charles III had died. He was previously diagnosed with cancer.
The ping of death is a protocol attack. Like a digital mail bomb, the target system crashes after opening it.
To avoid this ping of death issue, the malicious data from the attacker would be fragmented to send malformed packets with a ping of death attack command. When the
Uncover the mechanics of the Ping of Death attack and learn strategies to fortify your system against this classic cyber threat. Act now!
- What Is The Difference Between Lonely And Solitary
- What Is Sports Nutrition Evaluation: Overview, Benefits, And
- What Snake Is Allowed As A Pet In The Us
- What Is The Type: Null From The Battle Tower’S Base Friendship
- What Is The Difference Between Muscle And Tendon
- What Run Should I Do | Types of Runs Every Runner Should Know
- What To Do With Duck Egg? – Surplus of duck eggs and no idea what to do with all of them
- What Is The Difference Between A4 And Us Letter?
- What Is The Prefix For Cooperation?
- What Is The Electron Configuration Of Na ?
- What Is The Difference Between Vermutungen Aufstellen